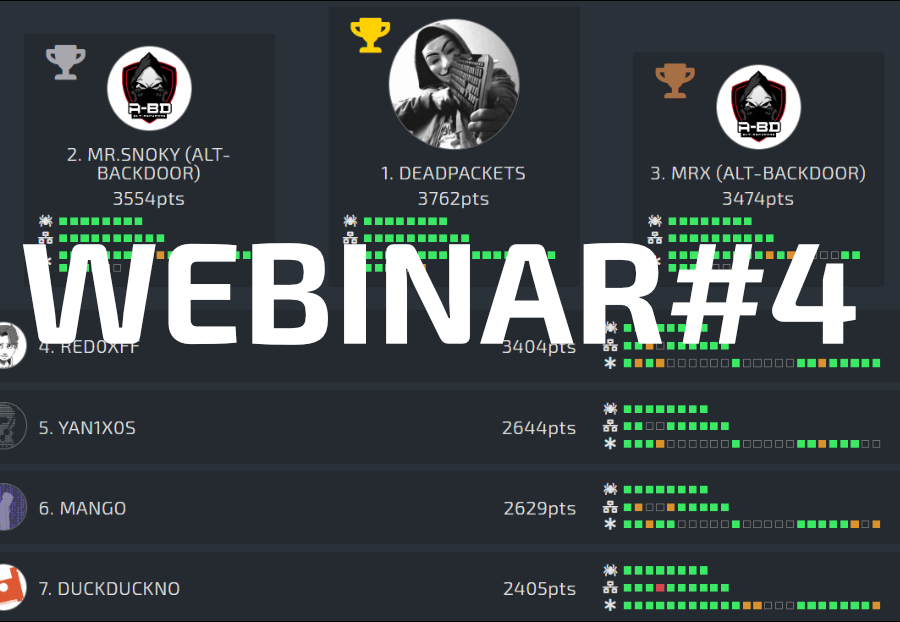
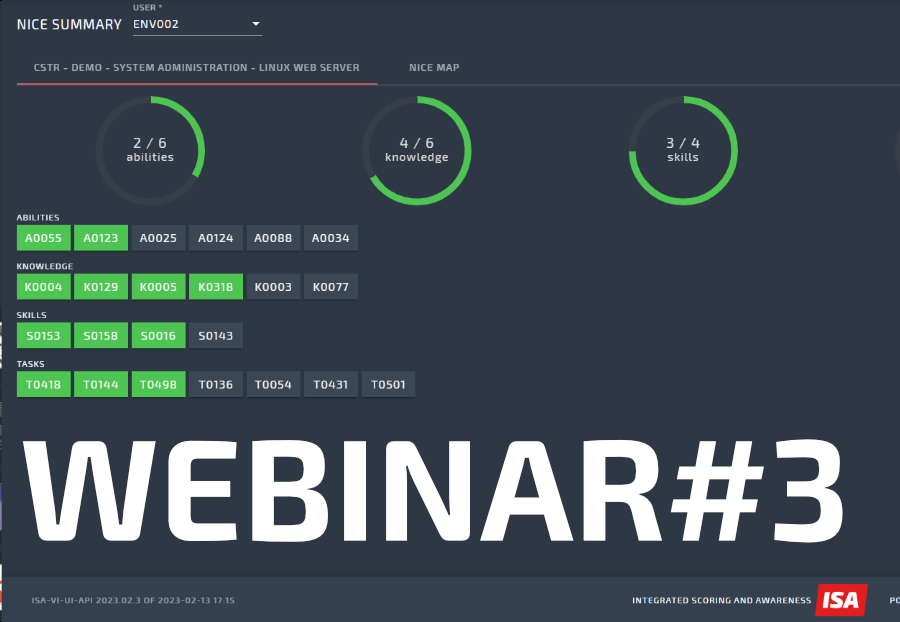
Live-Fire Exercises
Live-fire exercise is a deep technical Red vs Blue exercise designed for practicing response to a cyber crisis according to a realistic pre-defined scenario. It helps cybersecurity professionals simulate and practice defending against real-world cyber attacks. It helps to train the entire team to work together to practice not only their technical skills but also the team spirit necessary in responding to cyber attacks rapidly and effectively.

Threat Hunting Exercises
“Threat hunting” is a type of cyber range exercise where a team of cybersecurity experts works together in a simulated environment to find and stop threats before they do any harm to people or systems. It’s much like detectives searching for clues in a crime scene; the cybersecurity team looks for clues and evidence of suspicious activity that can be anything from computer viruses to hackers trying to steal information.

Capture the Flag Exercises
A capture-the-flag (CTF) exercise is a simulated cybersecurity competition that challenges participants to find and exploit vulnerabilities in a computer system in order to “capture a flag”. The “flag” may be a specific piece of data or code hidden within the system. Participants will rehearse working seamlessly together, and they may need to use a variety of skills and techniques. The teams may also need to defend their own systems against attacks.

Red/Blue Exercises
A red/blue team exercise is a simulation of a cyberattack, where two teams – the red team and the blue team – are pitted against each other. The red team represents the attackers, while the blue team represents the defenders. The exercise takes place on a cyber range that simulates the real-world IT infrastructure that the organization is looking to protect.
Meet our happy customers
Neste
The exercise was a great way to improve our handling of cyber incidents. We learned how to react quickly and efficiently to contain and mitigate threats, and we now feel better prepared to respond to real-world cyber attacks
-Jesse Titta, Cyber Security Operative – Neste Oyj

Heineken
I would really recommend other organizations to join an exercise like this.
-Coen Stennbeck, Information Security Officer at Heineken Netherlands

Estonian Public Broadcasting
The blue vs red setup was a great way to simulate real-world cyber threats, and it helped us develop our detection and prevention skills. It was also great to see the friendly competition between blue teams and how cooperation initiatives helped us gain bonus points.
– Madis Lauri, Software Application Architect – ERR

Description
Want to try out a cyber range event or organize one for your client? Our services are available with no long term commitments, just get in touch with us and let’s discuss your specific requirements.
With our cyber range technology, we will create a sophisticated virtual environment for you that can be tailored to mimic different IT systems. Essentially, the cyber range imitates the real-life IT infrastructure and allows you to see where it might be exploited.
Resources
CTF (capture the flag) is a mission-based learning, playing and […]
Cyber skills testing helps companies and organisations with recruitment. Instead […]
A red/blue team exercise is a simulation of a cyberattack, […]
Recent news
July 9, 2024
At CybExer Technologies, we are committed to providing global organizations with advanced tools to help them improve their security posture and boost cyber resilience. We have just launched the Digital […]
June 17, 2024
CybExer Technologies, together with Auve Tech, the City of Tartu, and the University of Tartu, unveiled a unique Smart City Cyber Range, which aims to enhance the cyber resilience of […]
February 9, 2024
CybExer Technologies, in partnership with e-Governance Academy, is delivering a set of tailored cybersecurity training programs for professionals working in Georgia’s Defence Forces. The program is being executed under the […]