
What’s the Process Behind Red/Blue Team Exercise?
A red/blue team exercise is a simulation of a cyberattack, where two teams – the red team and the blue team – are pitted against each other. The red team represents the attackers, while the blue team represents the defenders. The exercise takes place on a cyber range that simulates the real-world IT infrastructure that the organization is looking to protect.
A red/blue team exercise is typically facilitated by an instructor who is responsible for planning and preparing the exercise, selecting the participants for each team, and providing guidance to the participants throughout the exercise. The participants in the exercise are typically IT professionals or security personnel who are responsible for securing the organization’s IT infrastructure.
At the start of the exercise, the instructor provides a briefing to both teams. The red team is briefed on the target organization’s IT infrastructure, vulnerabilities, and attack vectors, while the blue team is briefed on the red team’s tactics, techniques, and procedures (TTPs).
The red team then begins executing their attack, using various attack methods such as phishing, social engineering, malware, and exploitation of vulnerabilities.
The blue team works to detect, respond, and mitigate the attack using tools and techniques such as intrusion detection systems, firewalls, and security information and event management (SIEM) systems.
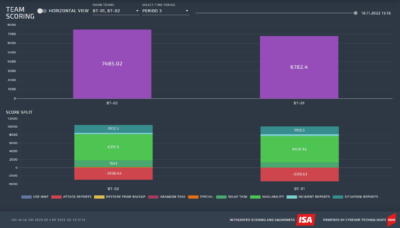
Team scores breakdown & total, all teams
Each column represents each Blue Team’s score breakdown in a given period for each of the currently applied scoring categories: Availability (green), Incident Reports (light blue), Situation Reports (dark blue), Attacks (red), Restores from Backup (yellow) and Special (orange). In addition, Overall Score (purple) is provided.
Throughout the exercise, the instructor provides guidance and feedback to both teams, helping them to improve their performance and adapt to new challenges. The instructor may also introduce new scenarios or challenges to the exercise to test the participants’ ability to adapt and respond to evolving threats.
After the exercise is complete, the instructor conducts a debriefing session with the participants. During the debriefing, they discuss their observations, lessons learned, and areas for improvement. This feedback helps participants to learn from their mistakes and improve their performance in future exercises.
The instructor plays a crucial role in providing guidance to both teams and ensuring that the exercise is conducted safely and effectively. They may also introduce new challenges or scenarios to the exercise to test the participants’ ability to adapt and respond to evolving threats.
In summary, a red/blue team exercise is a valuable training tool for IT professionals and security personnel to improve their skills and prepare for real-world cyber threats. By simulating a cyberattack in a controlled environment, participants can learn how to detect, respond, and mitigate cyber threats, improving the overall security of their organization’s IT infrastructure.

