
Hunting Threats on a Cyber Range
‘Threat hunting’ is a type of cyber range exercise where a team of cybersecurity experts works together in a simulated environment to find and stop threats before they do any harm to people or systems. It’s much like detectives searching for clues in a crime scene; the cybersecurity team looks for clues and evidence of suspicious activity that can be anything from computer viruses to hackers trying to steal information.
In a threat hunting exercise, the cybersecurity team will use a variety of tools and techniques to scan the cyber range, such as network sniffers, packet analyzers, endpoint detection, and response systems.
They will analyze the data they collect to find signs of threats, such as unusual network traffic or suspicious files. Once they have identified a potential threat, they will investigate further to determine the nature of the threat and the potential impact it could have on the system.
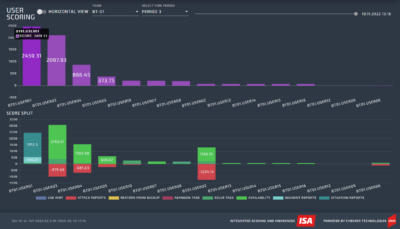 Individual score breakdown and total, one blue team
Individual score breakdown and total, one blue team
Each column represents each member of a Blue Team with score breakdown in a given period for each of the currently applied scoring categories: Availability (green), Incident Reports (light blue), Situation Reports (dark blue) and Attacks (red). In addition, Overall Score (purple) is provided.
What are threat hunting exercises used for?
Threat hunting exercises are useful because it helps the cybersecurity team to practice their skills and develop new ones. They learn how to work together effectively, how to use different tools and techniques to hunt for threats, and how to make decisions quickly and accurately. It also allows them to identify weaknesses in the system and develop strategies to address them.
Most importantly, the threat hunting exercise helps improve the team’s ability to respond to real-world cyber threats. It teaches them to be proactive rather than reactive, so they can prevent attacks before they happen rather than simply reacting to them after the fact.
Individual score breakdown and total, one blue team.
Each column represents each member of a Blue Team with score breakdown in a given period for each of the currently applied scoring categories: Availability (green), Incident Reports (light blue), Situation Reports (dark blue) and Attacks (red). In addition, Overall Score (purple) is provided.
Here’s an overview of a typical threat hunting exercise on a cyber range:
- Planning: As first, the objectives, scope, and timeline will be defined. This includes defining the simulated threat scenario, the assets to be protected, and the tools and techniques to be used.
- Preparation: As next, the cyber range environment will be prepared by setting up the network, systems, and applications to be used. This may involve creating virtual machines, configuring firewalls and intrusion detection systems, and installing software tools for threat hunting.
- Execution: Once the cyber range environment is ready, the threat hunting exercise can begin. The team of threat hunters will actively search for signs of malicious activity by analyzing network traffic, system logs, and other sources of data. They will use a variety of techniques such as anomaly detection, signature-based analysis, and behavioral analysis to identify potential threats.
- Response: Once a threat is identified, the team will take action to contain and mitigate the threat. This may involve isolating affected systems, blocking malicious traffic, or patching vulnerabilities.
- Analysis: After the threat hunting exercise is complete, the team will analyze the data collected to identify patterns and trends. This can help to identify weaknesses in the network and inform future threat hunting exercises.
- Reporting: Finally, the results of the threat hunting exercise are reported to stakeholders. This includes a summary of the findings, the actions taken to mitigate threats, and recommendations for improving the network’s security posture.
A threat hunting exercise on a cyber range is an effective way to proactively identify and respond to potential cyber threats in a controlled environment. By conducting regular threat hunting exercises, organizations can improve their ability to detect and respond to real-world cyber attacks.
TOPICAL: see the CybExer Webinar #2 about threat hunting exercises.

