A cyber range is a simulated environment that is used to train cybersecurity professionals and test an organization’s incident response capabilities. Cyber ranges typically include simulated network infrastructure, systems, and tools – as well as various types of cyber attacks.
- Help assess organization’s cyber readiness in realistic cyber attack scenarios and identify areas for development
- Improve and practice team collaboration skills in simulated cyber attack scenarios
- Address individual cyber skills development needs
- Measure the effectiveness of cyber training efforts
Our Approach to a Cyber Range
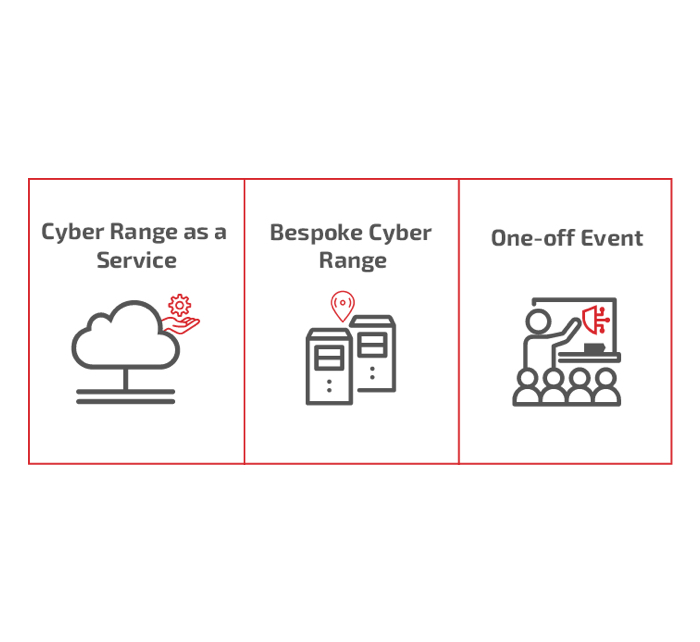
1. Solution Type
CybExer Technologies offers three main solution types that customers can choose from based on their needs, budget and limitations. Cyber Range can be selected as a service, as a completely bespoke solution or our customers can use Cyber Range for one-off events such as training and exercises.
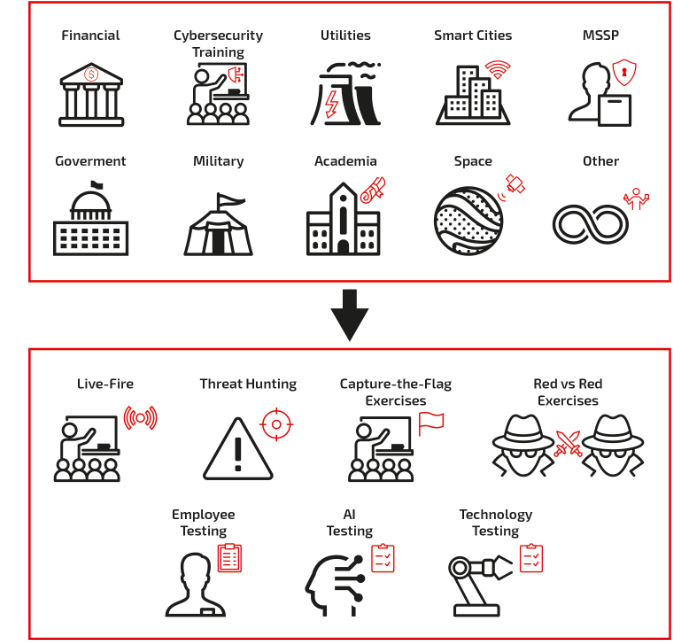
2. Industry & Use Cases
Cyber Range customers are different. They can represent different types of industries and they may be looking for different kinds of use cases – that suit their particular needs.
CybExer Technologies offers wide variety of both industry and use case options. When it comes to industries, we do have specific solutions, content and approach that we can offer to banking, government, smart cities, space, utilities, telcos, academia, training companies and managed security service providers.
We encourage you to contact us since the cyber range capabilities are endless.
3. On-demand Content Library & Customization
After the planning phase, the next step in setting up CybExer’s cyber range is to decide on the specific content setup. We are geared to guarantee our customers with quick wins and ability to start using the cyber range immediately, seamlessly and with minimal effort. We are able to offer our customers ready-made content or create the content from scratch.
The content creation is largely about technically defining the systems, the training scope, the attack and defence activities and more.
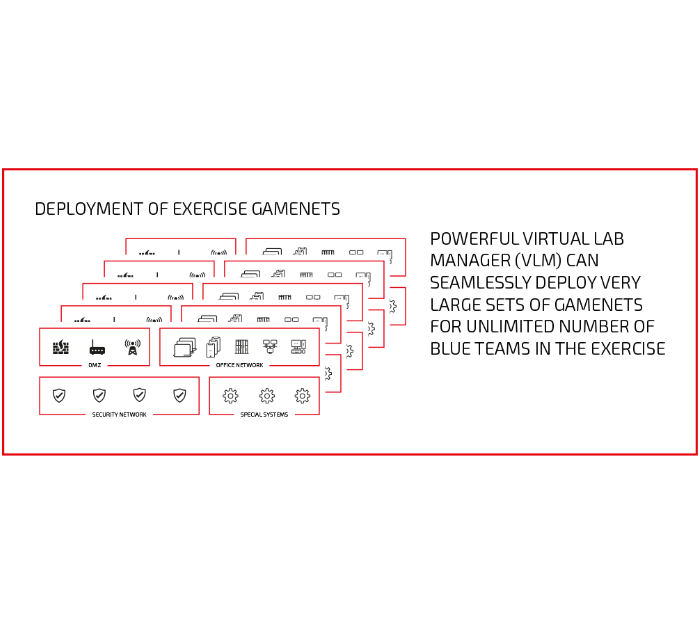
The secret of successful content orchestration lies in our powerful web-based virtual lab manager. It can seamlessly deploy very large sets of environments for an unlimited number of teams or individuals regardless of their use case (employee testing, live-fire exercise blue team – red team training activities, environments to train AI algorithms etc.).
CybExer can accommodate technically highly complex scenarios covering various types of IT systems: internet-facing services (DMZ), office networks, security networks, special systems such as OT, SCADA, military IT, etc. and even the most comprehensive and realistic technical set-ups for the exercise.
On the other hand, for classroom training on a specific topic, we might not even need very complex environments. For instance, if we are training Windows engineers to secure the Windows Active Directory service, perhaps we will only need a domain controller, a few workstations and a few servers.
4. Cloning Environments for Users
Once the use case and content for the customer have been agreed, CybExer’s Cyber Range allows rapid cloning of the necessary environments without limitations. The environments can be discarded rapidly – once a particular use case has exhausted itself, allowing new use cases and environments to be brought to life on the cyber range. This type of technology allows customers extreme flexibility.
This is where scalability comes into play – with a large number of users, use cases, environments – the cyber range can become really sizeable. For instance, if a customer has 30 blue defender teams on a national exercise, and each team has 100 virtual machines to defend, the cyber range must be capable of running 3,000 virtual machines at the same time.
Our Cyber Range allows the users to be at the same location or join the exercise from different locations around the world. Based on the customer’s needs, environments may also include virtualized and/or physically connected special systems. Read more about our research & development activities on physically connected devices, that span from HVAC to power-grid, oil and gas, military and space technology.
CybExer has developed an easy-to-use web-based tool for the cyber range operator to swiftly take care of the content-cloning process. The operator may belong to the customer’s own personnel, or in the case of cyber ranges purchased as a service or as an event, CybExer’s expert serves as the operator. Read more on our vLab Manager.
5. Powerful Visualization and Integrations for Real-Life Training Experience
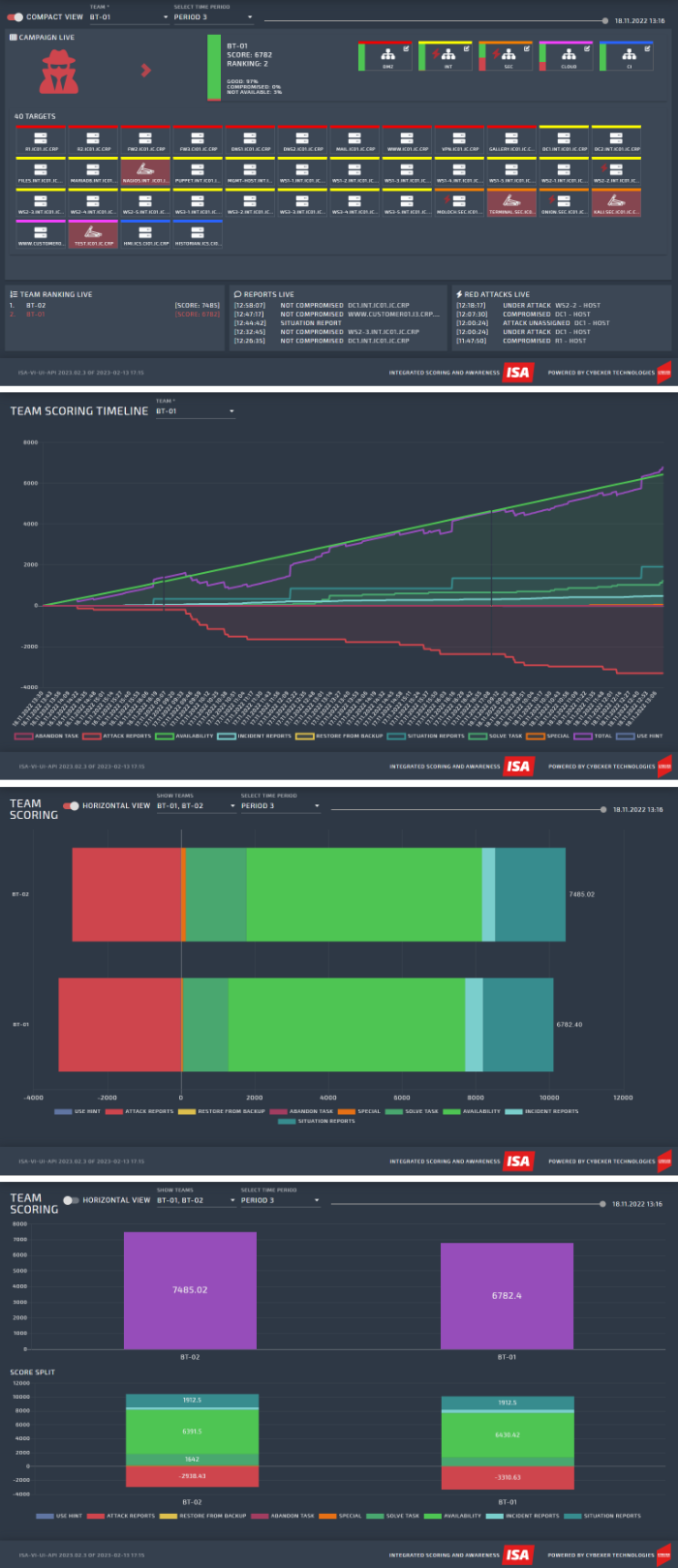
One important component of CybExer’s cyber range approach is value-adding services, starting with powerful, NATO-awarded situational awareness visualization dashboards.
Let us take example of utility of a visualization solution during a large-scale exercise. While the team that participates in the training exercise might perhaps only look at its own score and progress, the exercise control team has a powerful tool to direct and conduct the exercise, knowing at any given time about any given attack against any given system deployed on the cyber range. This is not only a convenience, but it helps to change the nature of the cybersecurity exercise: it will make the experience more dynamic, more immersive, more realistic. The exercise control is based on the visual data that they can see, can conduct effective media campaign, guide and manage the red team and if need be, effectively engage and escalate to the executive level. Visualization solution plays an important role in exercise “hot washup”, where the participants can have step-by-step detailed overview of the exercise events and the training experience. It is also an effective tool to brief guests, executives and VIPs on the activities conducted on the cyber range, helping to breach the “interface lag” that sometimes exists between the technical and management levels.
In the field of skills gap management, a powerful visualization solution can help organizations to have an effective overview of the skills and capability gap, making it thereby more manageable and more understandable. Solution can be used for benchmarking as well.
To demonstrate a very practical advantage of having a powerful visualization solution as an enabler, let us share a little war story by Ragnar Rattas that stresses the importance of careful design of the cyber range exercises at every step of the way – “We ran an exercise where a red team was carrying out a ransomware campaign against blue teams. The red team was quite successful, and their ransom demands, in bitcoins, were escalated to the management team. Somewhat surprisingly, the CEO refused to pay the ransom. Why? Turned out that there was no wallet address where the bitcoin ransom should have been paid; it had accidentally been left out of the exercise design.
The logic behind the CEO’s decision not to pay the ransom was that the missing wallet address indicated that the attacker’s idea was not to demand money in the first place but something else, in other words that the whole ransom campaign was a false flag.
Hence a small mistake in the design of the exercise led to a totally different interpretation of the ransom situation from that originally intended – an important lesson in very careful and thorough planning when designing exercise scenarios. The devil is in the details.”
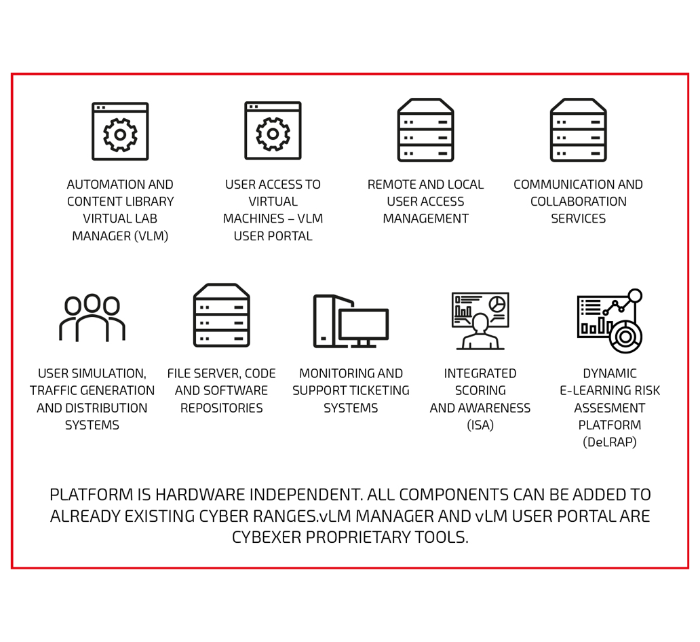
6. Underlying Cyber Range Platform
Everything discussed so far has been mostly about content, use cases and services. Yet none of this would happen without the technology part, which in CybExer’s Cyber Range offering has been organized into two logically separate pieces: the cyber range platform (IT services that make up the cyber range) and the cyber range infrastructure, which may consist of on-premises equipment, cloud-hosted infrastructure or both.
CybExer’s Cyber Range platform includes several functionalities developed specifically by CybExer such as the already mentioned situational awareness visualization tool and the operator’s cloning tool in addition to other tools and services that are needed for hosting a cyber range event. Read more about our cyber range platform here.
7. Cyber Range Infrastructure
Underneath the platform there is the IT infrastructure necessary for running cyber ranges. Our software as a service solution for Cyber Range takes away the hassle that a customer may have in running an underlying IT infrastructure for cyber range. The benefit of a SaaS cyber range lies in the fact that now the customer can focus more on the content, quick wins and immediate usability of cyber range. Cyber Range as a Service offers multiple ways for exchange of content, benchmarking and other advanced services.
In some cases, certain customers require bespoke cyber ranges. In that event, the customer´s equipment has been located at the customer’s own premises, at their cloud provider’s environment or as a hybrid system, where the infrastructure is a combination of on-premises equipment and cloud-hosted solutions. It is important to say that CybExer Cyber Range Platform is IT infrastructure-agnostic and can run on most commercial hardware solutions. It is not uncommon that customers who wish to have a bespoke cyber range, provide their own hardware necessary to run the cyber range through their own vendors. Here, CybExer Technologies’ experts are ready to consult our customers the requirements and specifications of the cyber range. If you are considering purchasing cyber range IT-infrastructure, we are ready to consult you in the process. You can contact our experts here.
Resources
CybExer Skills Testing offering covers testing services to support recruitment […]
Cyber Range has multiple definitions that may vary a lot. […]
Increasing accessibility: CybExer’s shift towards a SaaS delivery model Cyber […]