
Red Team Exercise in Cyber Security
Information security and threat prevention pose significant challenges for organizations worldwide. Recent research indicates that a staggering 4.1 million websites are infected with malware at any given time.
Organizations increasingly focus on optimizing threat detection and response processes rather than attack prevention. Practicing is the key when it comes to detecting and responding to these kinds of cyber threats and challenges.
That’s why the red team exercise is one of the most effective cybersecurity exercises for preparing your team for real-life cyber attacks. This article will explain what the red team exercise means, why it is important for organizations, and how it works.
What Is a Red Team Exercise in Cybersecurity?
According to the National Institute of Standards and Technology (NIST) glossary, Red Team Exercise refers to “an exercise, reflecting real-world conditions, that is conducted as a simulated adversarial attempt to compromise organizational missions and/or business processes to provide a comprehensive assessment of the security capability of the information system and organization.”
In simpler terms, it involves cybersecurity professionals coming together to simulate adversarial actions, challenging various cybersecurity controls. Their objective is to identify vulnerabilities in people, processes, and technology, with the goal of gaining unauthorized access to the organization’s assets.
What’s the Difference Between Red Teaming and Penetration Testing?
Penetration testing refers to a simulated cyber attack against a computer system, which is used to check for exploitable vulnerabilities. Generally, organizations use penetration testing to elevate a Web Application Firewall.
In the red team exercise, on the other hand, participants play the role of threat actors, trying to break the system and get far into their targets as much as they can.
In this case, the blue team (the majority of the organization’s IT team) is not aware that the simulated attack is happening, making the exercise more of a real-life experience. Therefore, the red team’s methods cover social engineering, phishing methods, and different attempts to enter the premises.
Penetration testing typically focuses on system assessment, while red team exercises evaluate the entire organization, including processes, technical controls, and training.
Why Is It Important to Conduct a Red Team Exercise?
Red team exercises are crucial for preparing organizations to defend against the most prevalent threats specific to their industry, such as ransomware attacks and data breaches.
In this day and age, it is essential for organizations to know about different types of possible attacks according to the industry they operate in. That way, it is easier to prioritize types of exercises and time for tests.
That’s why organizations must take time to choose the right cyber exercise partner that will help them understand what kinds of tests they should be doing based on their business.
Benefits of Conducting a Red Team Exercise
Conducting a red team exercise comes with a lot of benefits. Practicing is the key component to effectively train the team and detect possible threats. There is no better way to learn about your organization’s strengths and weaknesses than by continuously testing your staff’s skills and making sure your organization’s cyber readiness is high.
That being said, the most important benefits of conducting a red team exercise are the following:
-
Learn About Your Weaknesses and Identify Areas for Improvement
The red team exercise gives organizations a unique ability to identify the areas for improvement in their defense systems. This way, it’s easier to understand which security tools you should be working with when it comes to ensuring your organization’s effective operations and cyber resilience.
-
Measure Overall Cyber Readiness of Your Organization
Measuring progress is one of the most significant factors for steady growth. You never know when the threat or attack will occur, making it hard to prepare with a proper response.
A red team exercise will help you to properly measure the detection capabilities of the staff, process, and technology. If the team is prepared to identify and detect those threats, it can benefit the organization by preventing risks on time.
-
Improve Your Company’s Response Capabilities
Detection and response are directly tied to one another in this scenario. More red team exercises mean improved response time and quality. This way, organizations are trained to detect threats in minutes, giving them the ability to react faster and make important decisions on time.
-
Test Your Assumptions About Security
Most of the organizations worldwide assume they have security controls in place because they purchased them. That might be a wrong approach in many cases, as attackers are developing new practices to harm organizations.
It is absolutely vital to test your assumptions and ensure the effectiveness of your security controls by testing them through different red team exercises.
-
Stay One Step Ahead of Hackers
If your organization is constantly testing against possible attacker’s behaviors, it will make it easier to understand what is actually working. You should be aware of the advantages your team has to continue proper training in other fields.
How Does the Red Team Exercise Work?
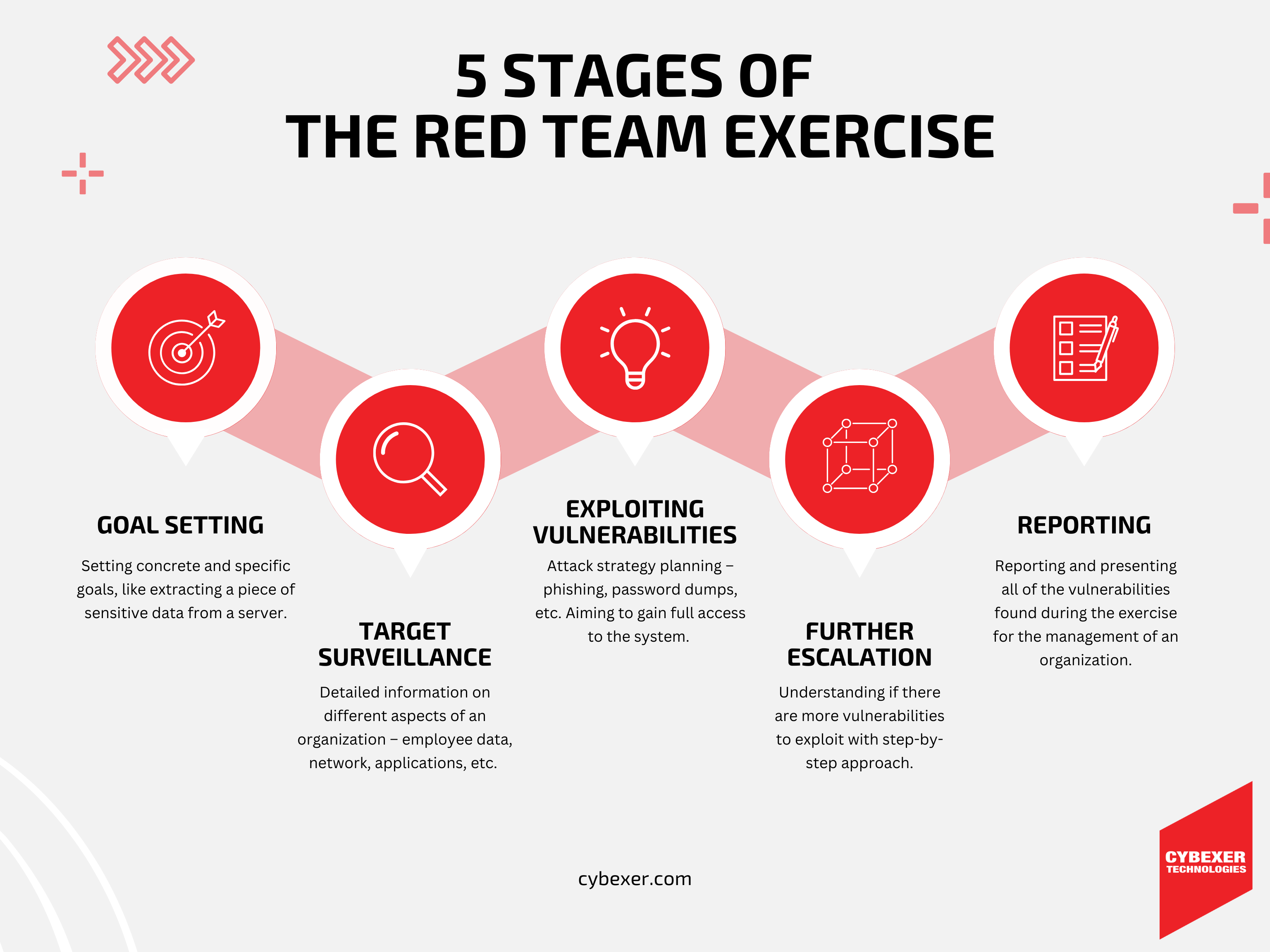
5 Stages of the Red Team Exercise
Generally, the red team exercise can be broken down into five different stages. Those stages are as follows:
- Goal setting – everything starts with a primary goal-setting session for the red team. It can be very concrete and specific, like extracting a piece of sensitive data from a server.
- Target surveillance – after the goals are set and objectives are clear, the team receives detailed information on different aspects of an organization, such as employee data, networks, applications, and physical spaces.
- Exploiting vulnerabilities – this is where the team starts planning different attack strategies, such as phishing, password dumps, etc. The goal is to gain full access to the system and start the attack.
- Further escalation – the red team will try to go further in this case and understand if there are more vulnerabilities to exploit. This process usually has a step-by-step approach to figuring out how far they can go.
- Reporting – this is one of the most critical parts of this exercise. After the attack, the red team has to properly report all of the vulnerabilities they found so the organization can address those to avoid attacks in real life.
What Should Be an Outcome of a Red Team Exercise?
Organizations should look at the red team exercise as an assessment session to test their abilities to prevent, detect, and respond to real-world attacks. The final report should give in-depth information and guidance on what your organization is lacking to meet modern security standards.
The assessment should provide tangible data to have a clear idea about preventive controls you need to implement to identify threats, the time it takes for your team to eliminate threats, and what issues need to be addressed in the future.
FAQ
What Is Red Teaming?
Red teaming in cybersecurity involves security experts and professional hackers simulating attacks to test an organization’s defense capabilities in real-life scenarios.
What Does a Red Team Member Do?
Red teams in cybersecurity typically consist of offensive security professionals who have knowledge and expertise in attacking systems and breaking into various defenses.
How to Become a Red Team Member?
In order to become a red team member, it is important to have a deep knowledge of cybersecurity and primary programming languages. It is also beneficial to have the experience of working as part of a blue team.
What Are Red Team Scenarios?
Different frameworks that companies use to assess their security level and cyber resilience are red team scenarios.
How Long Does the Red Team Exercise Take?
The duration of a red team exercise depends on factors such as technology complexity, physical location, employee count, and technical infrastructure, typically ranging from two to six weeks.
Selecting a Red Team Exercise Partner – CybExer Technologies
Choosing the right partner for running a successful red team exercise is vital for organizations worldwide. It can be very useful to have a trustworthy partner that gives you the tools and resources necessary to test your networks and spread awareness among your team members on how to act when cybersecurity incidents occur.
By leveraging cyber range technology, organizations can enhance their cyber defense capabilities and overall resilience. CybExer has been a pioneer in the industry since 2016, offering advanced Cyber Range technology to help organizations prepare for and address evolving cyber challenges.
If you wish to learn more about how CybExer can assist your organization, schedule a consultation with our cyber range experts to discuss your specific needs.

